It seems that there’s always a hacking story in the news, the most recent being a hack of Twitter accounts which you’ve likely read about. Hackers had managed to con a couple of Twitter employees into giving them access to their credentials. They used these credentials to make their way past security and sending out some bogus tweets – from some pretty big-name accounts, including Bill Gates, Elon Musk, and Apple – that linked to a bitcoin scam. To some extent, this attack seemed pretty ludicrous, but given how so much important information is conveyed via tweets these days, the ease with which the hackers managed to breach Twitter security and make some trouble is sobering.
And, of course, gets me thinking about how hackers can do some truly terrible damage. One of the most critical areas where hackers could do major harm is industrial control systems, which pretty much oversee all elements of our most vital infrastructure and industrial production. Think power generation, water treatment facilities, transportation systems, defense…If these systems get hacked, the damage could be far greater than a few folks getting duped into buying/selling cryptocurrency.
Security experts are continuously looking for new and better way to prevent hackers from succeeding. In (virtually) thumbing through some (virual) back copies of Spectrum IEEE, I came across one approach that seems promising. In her post, New Approach Could Protect Control Systems from Hackers, Michelle Hampson wrote about an “algorithm [that] creates ‘background noise’ during data transmission to alert officials to hacking.”
Because the major industrial control systems transmit data so rapidly, “hackers need interfere with the transmission of real-time data only for the briefest of moments to succeed in disrupting these systems.” The example Hampson uses underscores the seriousness of these types of threats: the 2010 Stuxnet attack in which hackers damaged over a 1000 centrifuges used in Iran’s uranium enrichment factory. Researchers have now developed a new means to quickly figure out that an incursion is occurring so that a system can be shut down before too much harm comes to it.
The researchers – Zhen Song of Siemens and his colleagues – drew on “the concept of “watermarking” data during transmission, a technique that can indicate when data has been tampered with” and applied it to industrial control systems.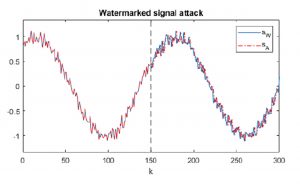
When hackers try toying with how data are being transmitted, the watermark signal is altered and the system is alerted that it’s under attack.
The approach involves the transmission of real-time data over an unencrypted channel, as conventionally done. In the experiment, a specialized algorithm in the form of a recursive watermark (RWM) signal is transmitted at the same time. The algorithm encodes a signal that is similar to “background noise,” but with a distinct pattern. On the receiving end of the data transmission, the RWM signal is monitored for any disruptions, which, if present, indicate an attack is taking place. “If attackers change or delay the real-time channel signal a little bit, the algorithm can detect the suspicious event and raise alarms immediately,” Song says.
Initial tests have been promising.
Whatever thwarts hackers from damaging the world, I’m all for it!
